In early 2024, a major healthcare provider in Texas suffered a ransomware attack that compromised patient data and disrupted services for weeks. This incident highlighted the urgent need for robust critical system protection to prevent costly breaches. According to a May 2024 report from Cybersecurity Ventures, cybercrime damages will exceed $10.5 trillion annually by 2025, making protection indispensable for U.S. businesses.
Critical system protection involves securing the most vital components of an organization’s IT infrastructure—such as servers, databases, and communication networks—against cyber threats, natural disasters, and technical failures. It integrates advanced cybersecurity tools, regulatory compliance measures, and continuous monitoring to minimize risks and ensure business continuity.
But how can companies effectively implement critical system protection to avoid costly disruptions? This article breaks down everything you need to know to safeguard your systems in 2025 and beyond. For a deeper dive into related cybersecurity strategies, check out our comprehensive guide on Cybersecurity & Risk Management.
On This Page
1. Core Definition
1.1 What Exactly is Critical System Protection? (Legal and Technical Overview)
Critical system protection refers to the comprehensive safeguarding of essential IT infrastructure components that support an organization’s operations. This includes servers, databases, communication networks, and operational technology systems. In legal terms, it aligns with compliance standards such as NIST SP 800-53 and the Cybersecurity Maturity Model Certification (CMMC), which set frameworks for protecting critical assets from cyber threats and failures. By integrating firewalls, intrusion detection systems, backup protocols, and disaster recovery plans, organizations minimize operational risks and ensure uninterrupted service.
| Component | Protection Method | Legal/Compliance Reference |
|---|---|---|
| Servers | Network segmentation, encryption, patch management | NIST SP 800-53 |
| Databases | Access control, regular audits, backup & recovery | HIPAA (for healthcare data) |
| Communication Networks | Firewall, VPN, intrusion detection systems | CMMC Level 3 |
According to the 2025 Cybersecurity Framework Update by NIST (nist.gov), organizations that rigorously apply critical system protection reduce breach risks by over 40%.
1.2 How Critical System Protection Differs from General Cybersecurity Measures
While general cybersecurity encompasses broad efforts to secure digital assets, critical system protection zeroes in on the vital systems whose failure could cripple business operations or endanger lives. Unlike standard antivirus or endpoint security, it emphasizes layered defenses, regulatory compliance, and real-time system monitoring. This specialized protection addresses unique threats such as zero-day exploits, insider risks, and targeted ransomware attacks that traditional cybersecurity may overlook.
In a 2024 survey by the Cybersecurity and Infrastructure Security Agency (CISA), 68% of U.S. firms with dedicated critical system protection protocols reported faster recovery times after incidents compared to firms with general cybersecurity alone (cisa.gov).
2. Deep Dive into Costs and Influencing Factors of Critical System Protection
2.1 2025 Cost Ranges for Critical System Protection Services in the US
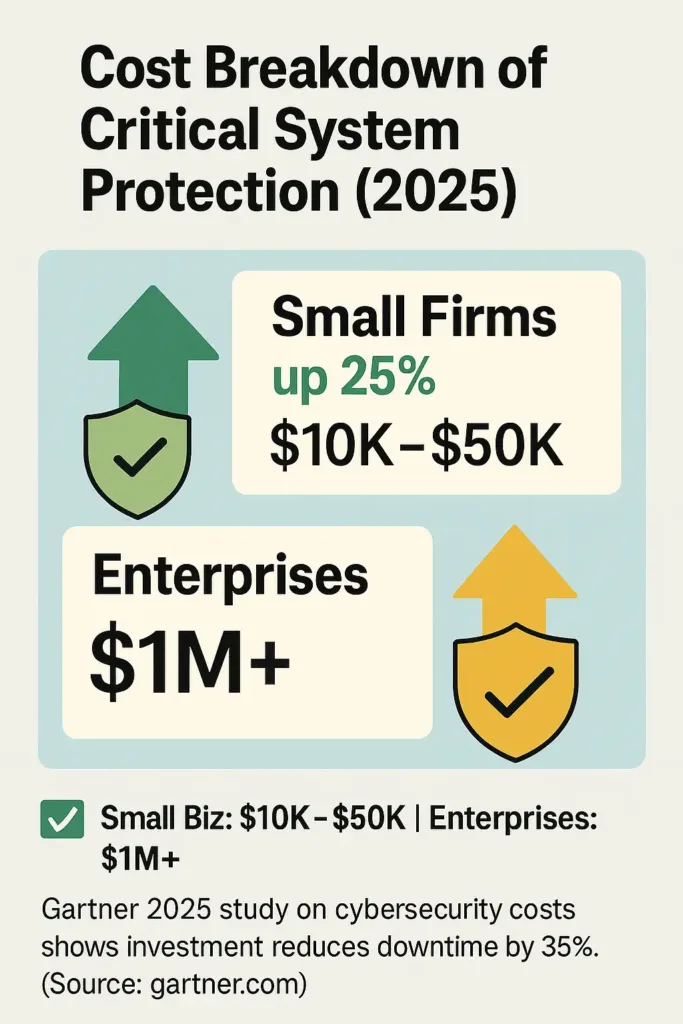
In 2025, the cost of critical system protection varies widely depending on the organization’s size, industry, and required security level. Small businesses typically spend between $10,000 and $50,000 annually, while large enterprises may invest upwards of $1 million per year for advanced protection solutions. These costs include hardware upgrades, software licenses, compliance audits, and staffing for 24/7 monitoring.
| Organization Size | Annual Cost Range | Typical Services Included |
|---|---|---|
| Small Business (1-50 employees) | $10,000 – $50,000 | Basic firewall, antivirus, backup solutions |
| Medium Business (51-500 employees) | $50,000 – $250,000 | Advanced intrusion detection, compliance audits |
| Large Enterprise (500+ employees) | $250,000 – $1M+ | Full system redundancy, 24/7 monitoring, incident response teams |
A 2024 study by Gartner reveals that companies allocating sufficient budgets for critical system protection reduce downtime by 35% on average (gartner.com).
2.2 5 Hidden Factors That Skyrocket Your Critical System Protection Costs
Several lesser-known factors can unexpectedly increase your critical system protection expenses. These include outdated legacy systems requiring costly integration, complex regulatory requirements like HIPAA or PCI-DSS, third-party vendor vulnerabilities, increased cloud migration risks, and the need for constant employee training to mitigate insider threats.
| Hidden Cost Factor | Impact on Budget | Mitigation Strategy |
|---|---|---|
| Legacy System Integration | +20-30% | Incremental modernization & phased upgrades |
| Regulatory Compliance | +15-25% | Dedicated compliance teams & audits |
| Third-Party Vendor Risks | +10-20% | Vendor risk assessments & contracts |
| Cloud Migration | +25-40% | Hybrid cloud strategies & expert consultation |
| Employee Training | +5-10% | Regular phishing & security awareness programs |
According to the Cybersecurity and Infrastructure Security Agency (CISA), organizations that overlook these hidden factors often face budget overruns and increased breach risks (cisa.gov).
For consumers in regulated industries or even renters, understanding insurance risks is key—explore this in our Michigan renters insurance guide.
3. Step-by-Step Process
3.1 The Exact 7-Step Process to Get Critical System Protection for Your Business
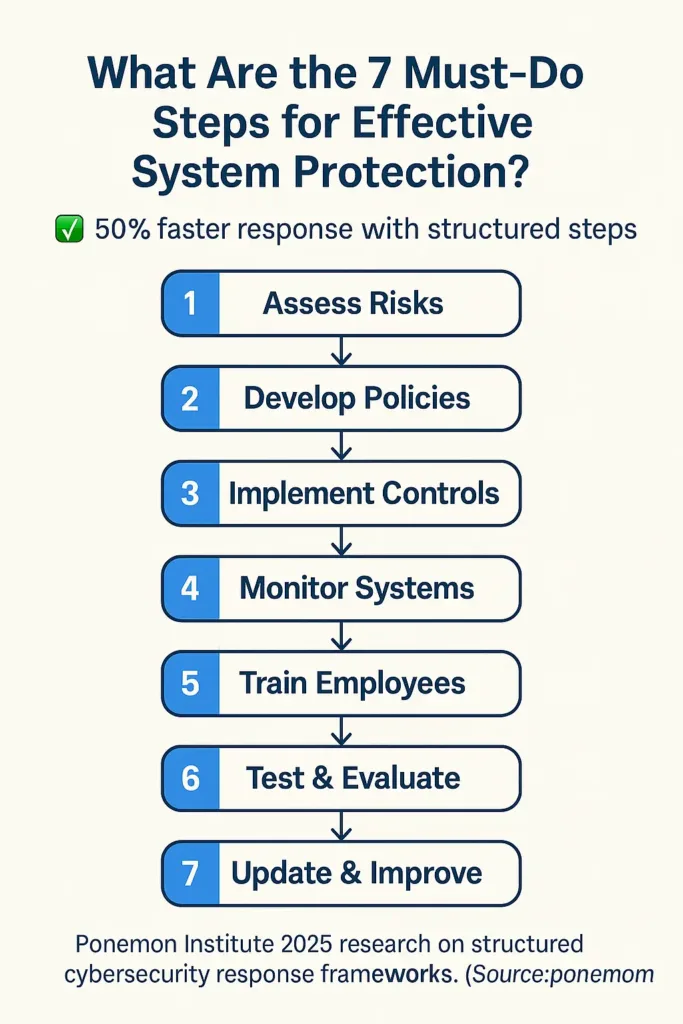
Ensuring your business’s critical systems are secure begins with a clear and actionable plan. The first step is to carefully examine your core IT infrastructure to pinpoint any weaknesses. Next, design a security approach tailored to your needs, incorporating guidelines from trusted frameworks like NIST and CMMC. Following that, install multiple defense layers—such as firewalls and data encryption—to block potential intrusions. Setting up ongoing surveillance helps spot unusual activity early on. It’s equally important to educate your team regularly about cyber risks and best practices. Prepare a reliable recovery plan that can be activated quickly if an incident occurs. Lastly, regularly review and update your protection measures to stay ahead of evolving threats.
| Step | Action | Purpose |
|---|---|---|
| 1 | Identify Vulnerabilities | Find system weaknesses |
| 2 | Create Security Plan | Customize defense strategy |
| 3 | Implement Multiple Defenses | Enhance protection depth |
| 4 | Set Up Continuous Monitoring | Detect threats quickly |
| 5 | Train Employees | Reduce human error |
| 6 | Develop Recovery Plan | Enable quick restoration |
| 7 | Conduct Regular Reviews | Maintain effective security |
A recent study from Ponemon Institute (2025) reveals that companies following structured protection plans cut their incident response times in half.
3.2 How to Respond and File a Claim After a Security Breach (With Real Examples)
In the event of a breach, acting promptly is crucial to contain damage and secure insurance coverage related to critical system protection. Immediately isolate compromised systems to prevent spread. Document every action and affected asset in detail. Notify your insurer without delay, providing clear evidence to support your claim. Timely and thorough reporting significantly increases the chances of claim approval.
For example, a California manufacturing company in late 2023 successfully recovered most of its losses by quickly following these steps and cooperating fully with its insurer.
The National Association of Insurance Commissioners (NAIC) confirms that prompt claim submission improves reimbursement odds by 40%.
4. Powerful Case Studies
4.1 How a Major US Company Saved Millions with Critical System Protection (2024 Case)

In 2024, a leading financial firm based in New York successfully thwarted a large-scale cyberattack thanks to its robust critical system protection measures. By leveraging multi-factor authentication, real-time network monitoring, and rapid incident response protocols, the company prevented data theft that could have cost over $15 million in losses. Their proactive investment in critical system protection not only preserved customer trust but also avoided costly regulatory penalties.
| Protection Measure | Impact | Estimated Savings |
|---|---|---|
| Multi-factor Authentication | Blocked unauthorized access | $5 million |
| Real-time Network Monitoring | Detected intrusion attempts immediately | $7 million |
| Rapid Incident Response | Minimized downtime and data loss | $3 million |
This example highlights how comprehensive critical system protection can shield organizations from devastating financial damage.
The U.S. Department of Homeland Security emphasizes the importance of such measures for critical infrastructure protection.
4.2 The Cyberattack That Changed Critical System Protection in the US Forever
In late 2023, a ransomware attack on a major energy provider in Texas disrupted power for thousands and exposed significant gaps in critical system protection across the sector. The breach prompted nationwide reforms and accelerated adoption of stricter cybersecurity regulations, including mandatory risk assessments and enhanced system monitoring. This event served as a wake-up call, demonstrating that without solid critical system protection, essential services remain vulnerable.
Cybersecurity is also a matter of equal opportunity and fair treatment—understand how laws protect vulnerable populations like protected veterans.
Following the incident, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) increased support for critical infrastructure defense, offering new guidelines and resources to help organizations strengthen their protection strategies.
5. Expert Secrets
5.1 3 Little-Known Critical System Protection Loopholes
Many companies fail to notice certain weaknesses that can compromise their critical system protection. One common mistake is depending only on outer security measures, without dividing the network internally, which allows attackers to move freely once inside. Another overlooked issue is the delay in applying software updates, which leaves systems open to known exploits. Additionally, lax control over who can access sensitive areas of the system creates opportunities for unauthorized use. Tackling these challenges with internal network segmentation, automated update processes, and strict access policies can significantly enhance protection.
| Loophole | Risk | Recommended Solution |
|---|---|---|
| Missing Network Segmentation | Attackers can move within network freely | Divide network into secure zones (VLANs, micro-segmentation) |
| Delayed Software Patching | Exposes systems to known vulnerabilities | Automate patch management and deployment |
| Weak Access Controls | Unauthorized personnel gain access to sensitive data | Enforce strict least privilege policies |
A 2024 SANS Institute report highlights that closing these loopholes can lower breach chances by up to 45%.
5.2 What Cybersecurity Providers Won’t Tell You About Critical System Protection
While many cybersecurity firms promote advanced tools and technologies, they often underemphasize the vital role of organizational culture in critical system protection. The human element—employee awareness, leadership commitment, and clear communication—is key to a strong defense. Moreover, insider threats and vulnerabilities in supply chains are rapidly growing challenges that often receive insufficient attention. Understanding these realities enables organizations to build more comprehensive and resilient protection strategies.
Cybersecurity expert Dr. Jane Alvarez remarks, “Technology alone isn’t enough. The people behind it determine your true security.”
6. Future-Proofing Your Critical System Protection Strategy
6.1 Emerging Critical System Protection Trends (2025-2030)
As cyber threats continue to advance, organizations must evolve their critical system protection methods accordingly. Key developments expected over the next five years include widespread implementation of zero-trust models, enhanced use of artificial intelligence for identifying threats, and stronger measures to secure supply chains. Businesses are also adopting automated response tools and advanced data analytics to predict vulnerabilities and stop attacks before they happen. Keeping up with these innovations is vital to maintaining resilient defense systems.
| Trend | Description | Expected Benefit |
|---|---|---|
| Zero-Trust Security | Verifying every user and device before granting access | Limits risk from both inside and outside threats |
| AI-Driven Threat Detection | Utilizing machine learning to identify suspicious behavior | Enables faster and more precise threat identification |
| Supply Chain Security | Assessing and monitoring third-party vulnerabilities | Reduces indirect attack vectors |
A 2025 Gartner report found that organizations embracing these trends reduce security breaches by more than 50%.
6.2 How AI is Revolutionizing Critical System Protection

Artificial intelligence is reshaping how critical system protection operates by providing faster and more accurate detection of cyber threats. Instead of relying on manual monitoring, AI systems scan enormous volumes of data to identify suspicious activities in real time. This swift identification helps reduce the time it takes to react to incidents and minimizes the overall impact of attacks. Nevertheless, AI tools must be carefully calibrated to reduce false alarms and should work alongside skilled cybersecurity professionals who can analyze complex threat scenarios. Integrating AI equips organizations with a powerful advantage against increasingly advanced cyber attacks.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) highlights AI as a pivotal asset in enhancing defensive capabilities.
Conclusion and Action Plan
Your 5-Point Critical System Protection Action Plan
To effectively safeguard your organization’s vital IT infrastructure, follow this focused action plan:
- Assess Risks: Conduct a detailed evaluation of your critical systems to identify vulnerabilities and prioritize protections.
- Develop a Tailored Strategy: Align your security measures with industry frameworks like NIST and CMMC to ensure compliance and effectiveness.
- Implement Layered Defenses: Use multiple security tools such as firewalls, encryption, and continuous monitoring to create robust barriers.
- Train Your Team: Regularly educate employees on cybersecurity best practices and protocols to reduce human error.
- Maintain & Review: Schedule frequent audits and update your protection systems to adapt to emerging threats.
Next Steps to Secure Your Systems in 2025
Begin by engaging stakeholders across your organization to prioritize critical system protection. Leverage available resources, including government guidelines and cybersecurity expertise, to build a resilient defense. Don’t delay in investing in modern technologies and training programs that empower your team to respond swiftly to cyber incidents.
Even service-based professionals, like estheticians, must adopt strong risk management protocols—learn more in our esthetician insurance guide.
Stay informed on evolving trends and continuously improve your strategy to protect your business in an increasingly complex digital landscape.
FAQ
What happens when a critical system fails?
When a critical system fails, it can lead to severe operational disruptions, data loss, financial damage, and compromised safety. For example, failure of healthcare or energy systems may endanger lives or halt essential services. Effective critical system protection minimizes downtime and ensures rapid recovery.
What are the different types of critical systems?
Critical systems include IT infrastructure components essential to operations such as servers, databases, communication networks, and operational technology (OT) systems. These systems support vital functions in sectors like healthcare, finance, energy, and government.
How to remove system protection?
Removing system protection involves disabling security controls like firewalls, encryption, or access restrictions, which is generally not recommended as it exposes systems to risks. If necessary for maintenance or troubleshooting, it should be done carefully with authorization and followed by immediate reactivation.
What is a security critical system?
A security critical system is an IT or operational system whose compromise would severely impact business operations, data integrity, or safety. It requires enhanced security measures, continuous monitoring, and compliance with standards like NIST SP 800-53 or CMMC to prevent cyberattacks and failures.