Last month in San Jose, Kevin—a mid-sized SaaS provider’s CTO—was blindsided when his cyber insurance claim was denied after a ransomware attack. His company had implemented Silverfort for identity protection, yet the insurer argued it wasn’t enough. “But we have zero trust!” he protested. It didn’t matter. The policy required layered controls far beyond that.
So what exactly does cyber insurance coverage with Silverfort include—and what doesn’t it cover?
Cyber insurance coverage with Silverfort often supports identity and access controls, but it doesn’t guarantee compliance with insurer requirements in 2025. According to NAIC, 83% of policies now demand risk controls beyond MFA, including endpoint protection and employee training.
Want to avoid a nasty surprise during your next audit or claim?
Here’s what you need to know if you’re relying on Silverfort and want to stay covered.
On This Page
1. What Is Cyber Insurance Coverage in the Context of Silverfort?
1.1 Why Silverfort Matters in Cybersecurity Programs
When Ashley, an IT director in Tampa, reviewed her company’s 2025 cyber insurance renewal questionnaire, she was confident. After all, they’d just deployed Silverfort across their hybrid infrastructure. But halfway through, she paused: Does this tool alone actually meet the insurer’s security control checklist? The truth is—Silverfort plays a critical role, but it’s not the whole picture.
Silverfort is primarily a Zero Trust access enforcement platform. It brings multi-factor authentication (MFA) and visibility to legacy systems, privileged accounts, and lateral movement, especially where traditional identity providers can’t go. That makes it attractive to insurers scanning for identity-centric risk mitigation.
Yet, from an insurance underwriting perspective, deploying Silverfort doesn’t automatically satisfy cyber insurance requirements. Cyber insurance coverage with Silverfort hinges not just on what the tool does—but how it’s configured, maintained, and embedded in a broader cybersecurity framework.
Pro Tip: Insurers want proof of how tools like Silverfort are operationalized—logs, policies, reporting—not just a license agreement.
1.2 What Cyber Insurance Actually Covers (And What It Doesn’t)
Cyber insurance coverage with Silverfort is often misunderstood. The insurance policy itself doesn’t “cover Silverfort” as a product; instead, it evaluates Silverfort’s presence as a control mitigating specific risk vectors—like credential-based intrusions or unauthorized lateral movement. If Silverfort helps reduce those risks, insurers may offer better terms.
Generally, cyber insurance covers:
- Data breach response (notification, legal, credit monitoring)
- Business interruption losses
- Regulatory fines and penalties
- Ransomware response (including negotiation and payment facilitation)
- Forensics and incident recovery
But it does not cover:
- Known vulnerabilities left unpatched
- Poor employee training outcomes
- Uninsured subsidiaries or third-party tools outside the policy scope
- “Silent failures” where detection tools were misconfigured
According to the NAIC Cybersecurity Model Law (2024 update), insurance claims tied to “failure of reasonable security measures” can be excluded—even if a tool like Silverfort is in place but improperly used.
Table: What Silverfort Covers vs What Insurers Cover
| Control Area | Silverfort Addresses | Insurer Covers It? |
|---|---|---|
| MFA & access enforcement | ✅ Yes | ✅ If documented |
| Lateral movement protection | ✅ Yes | ✅ If logs retained |
| Email-based phishing | ❌ No | ✅ If training in place |
| Endpoint detection & response | ❌ No | ❌ Not relevant |
| Regulatory compliance (HIPAA) | Partial | ✅ If full controls |
| Insider threat mitigation | ❌ No | ❌ If unmonitored |
1.3 Where Silverfort Fits Into Insurance Assessments
Underwriters in 2025 rely on a mix of quantitative questionnaires and qualitative interviews to assess risk. When evaluating identity controls, cyber insurance coverage with Silverfort may earn favorable scoring if:
- MFA is enforced across all assets, including legacy servers
- Risk-based access is applied to privileged accounts
- Audit trails can demonstrate real-time enforcement
However, Silverfort is usually just one line item in the broader evaluation matrix. Insurers often ask:
- What backup solutions are in place?
- Is there endpoint detection and response (EDR)?
- Is employee phishing training up to date?
- Are you following NIST 800-53 or CIS Top 18 frameworks?
That’s where things get tricky. Silverfort contributes meaningfully to identity security, but doesn’t replace controls for endpoints, email, backups, or staff awareness.
“A well-deployed identity solution like Silverfort checks boxes—but no tool checks them all,” says a 2025 report by the Cybersecurity and Infrastructure Security Agency (CISA).
Checklist: When Silverfort Helps You Pass an Insurance Audit
✅ MFA enforced across Active Directory and legacy systems
✅ Admin accounts monitored with behavioral analytics
✅ No reliance on passwords alone
✅ Access controls documented and logged
✅ Integrated with broader SIEM or SOAR systems
❌ No endpoint coverage without EDR
❌ No phishing protection unless external training is verified
2. Is Silverfort Enough to Meet Cyber Insurance Requirements?
2.1 Common Insurer Expectations in 2025
When Jordan, the CISO of a healthcare firm in Denver, sat down with their broker to renew the company’s cyber insurance, he assumed Silverfort checked the box. After all, it had drastically reduced lateral movement. But the underwriter’s response was blunt: “Where’s your endpoint protection? And what about phishing training logs?” The message was clear—Silverfort alone wasn’t enough.
In 2025, cyber insurance carriers require a layered security posture, not just a single point solution. Even when Silverfort is deployed, insurers still expect:
- Documented incident response plans
- Regular vulnerability assessments
- Employee awareness training
- Enforced MFA on all systems
- Endpoint Detection & Response (EDR)
- Third-party risk assessments
Cyber insurance coverage with Silverfort is considered a partial solution—strong on identity enforcement, but weak on other critical vectors like malware containment, patch management, or human error mitigation.
Stat to Know: According to a 2024 NAIC study, over 71% of rejected cyber claims were tied to gaps in areas unrelated to identity security—even in companies using tools like Silverfort.
Checklist: What Insurers Look for Beyond Silverfort
✅ MFA enforced across entire infrastructure
✅ Phishing simulations completed quarterly
✅ EDR solution with real-time alerting
✅ Secure backups and recovery testing
✅ Patch management logs available
❌ Silverfort alone is not endpoint protection
❌ Zero Trust ≠ full compliance
2.2 Comparing Silverfort to NIST and NAIC Compliance Baselines
The NIST 800-53 framework and the NAIC Cybersecurity Model Law are now standard touchstones for cyber insurance underwriting. The question insurers ask is not “Do you use Silverfort?” but rather, “Do your controls map to required frameworks?”
Here’s how cyber insurance coverage with Silverfort measures up:
| Requirement | NIST Ref. | Covered by Silverfort? |
|---|---|---|
| AC-2 (Account Management) | ✅ Partial | ✅ Yes (with policies) |
| IA-2 (User Authentication) | ✅ Core | ✅ Yes (strong MFA) |
| AU-6 (Audit Review & Analysis) | ✅ Essential | ⚠️ Limited |
| IR-4 (Incident Handling) | ✅ Mandatory | ❌ Not applicable |
| SI-4 (Monitoring, Detection, Response) | ✅ Mandatory | ❌ Needs SIEM integration |
Silverfort excels in authentication and access enforcement, but it doesn’t handle logging, alerting, or incident response in isolation. Most insurers expect a mature, mapped control environment, not a single-vendor solution.
“Zero Trust identity is a foundation—not a finish line,” notes a 2025 CISA guidance brief.
Pro Tip: When filling out cyber risk questionnaires, avoid listing only vendor names. Focus on controls and map them to frameworks (NIST, CIS v8, HIPAA). Silverfort should appear as one component of a layered defense.
2.3 Real Gaps Between Zero Trust and Insurability
Silverfort markets itself as a Zero Trust enabler—and rightly so. It adds tremendous value by enforcing identity-based policies on systems that normally resist modern MFA. However, cyber insurance coverage with Silverfort often breaks down at the boundary between theory and practice.
Here’s what insurers see as gaps:
- Human error: Silverfort doesn’t protect against a CFO clicking on a phishing email.
- Unmonitored endpoints: No visibility into device behavior without EDR.
- Shadow IT: Silverfort won’t detect unsanctioned apps or rogue access points.
- Recovery readiness: It doesn’t test backup reliability or incident drills.
Even within identity security, misconfigurations can derail coverage. For instance, if Silverfort’s policies are too permissive or not applied universally, the insurer may argue negligence.
Writer’s fingerprint: Let’s be honest—there’s a growing misconception in IT circles that buying a “Zero Trust” tool equals automatic insurability. But ask any underwriter in 2025 and you’ll hear a different story: “Show me the logs. Show me the training. Show me the backups.” That’s the bar now—not just branding.
Table: Where Silverfort Stops and Insurers Expect More
| Risk Category | Silverfort Handles | Insurer Demands |
|---|---|---|
| Unauthorized access | ✅ Strong control | ✅ Acceptable |
| Malware containment | ❌ No | ✅ Required |
| Data recovery testing | ❌ No | ✅ Mandatory |
| Human factor mitigation | ❌ No | ✅ Critical |
| Third-party vendor risk | ❌ No | ✅ Audit trail |
3. Pros and Limitations of Cyber Insurance Coverage with Silverfort
3.1 Strengths: MFA, Lateral Movement Protection, Visibility
When Malik, CIO of a financial services startup in Charlotte, had to present his company’s cybersecurity architecture to an insurer, he leaned heavily on Silverfort. “We’ve locked down lateral movement and legacy access with agentless MFA,” he said. The underwriter nodded—impressed but unconvinced. Still, Silverfort brought undeniable value to the table.
Cyber insurance coverage with Silverfort often shines in three areas:
- Multi-Factor Authentication (MFA): Silverfort enforces MFA on systems that traditionally lacked that capability—mainframes, legacy file shares, and custom-built apps.
- Lateral Movement Detection: It disrupts credential misuse by monitoring and halting unauthorized east-west traffic within networks.
- Visibility Across Identities: Silverfort provides centralized insight into privileged access and service accounts—two major insurer pain points in breach scenarios.
According to a 2024 CISA Zero Trust Progress Report, 64% of insurance-approved cybersecurity audits highlighted MFA coverage of non-web assets as a deciding factor—something Silverfort uniquely enables.
Table: How Silverfort Helps Reduce Insurer-Rated Risks
| Risk Vector | Silverfort Mitigation | Impact on Insurance Terms |
|---|---|---|
| Unauthenticated Legacy Access | ✅ MFA Enforced | ✅ Premium Reduction |
| Lateral Credential Abuse | ✅ Access Control Logs | ✅ Improves Risk Score |
| Privileged Account Abuse | ✅ Unified Visibility | ✅ Required for Approval |
| Email Phishing | ❌ Not Covered | ❌ No Effect |
| Endpoint Ransomware | ❌ Not Covered | ❌ No Effect |
Pro Tip: Want to impress underwriters? Provide access logs from Silverfort showing denied lateral moves or MFA enforcement success rates—not just configuration screenshots.
3.2 Limitations: Coverage Gaps, Blind Spots, Human Layer
Cyber insurance coverage with Silverfort is powerful—but not comprehensive. Its scope is identity-focused, which means it inherently leaves gaps that insurers still penalize.
Let’s be clear:
- Silverfort does not protect endpoints (laptops, phones).
- It won’t filter malicious email links or detect insider threats.
- It assumes the user’s behavior is safe—a risky assumption.
- It doesn’t include SIEM, SOAR, or full-scale incident response.
Underwriters in 2025 want to see layered resilience: MFA + EDR + backups + training. Silverfort can’t replace those. It’s a crucial puzzle piece, but not the whole picture.
NAIC’s Cybersecurity Law (as updated in 2024) stresses “the implementation of administrative, technical, and physical safeguards”—Silverfort supports only one of those three.
Dialogue: Cyber Broker vs Client
Client: “We use Silverfort for identity security. That should cover our cyber needs, right?”
Broker: “It covers some needs. But unless you’re also managing phishing risk, device controls, and recovery plans, your coverage might be partial—or rejected.”
3.3 What Insurers Are Looking for in 2025 (Beyond Silverfort)
Insurance providers no longer assess tech stacks—they assess resilience strategies. They’re not interested in vendor logos; they want to see:
- How MFA integrates with onboarding/offboarding
- Whether backups are tested regularly
- If patch cycles are enforced and monitored
- If phishing simulations result in retraining
Cyber insurance coverage with Silverfort helps answer some of those questions—but insurers need evidence of cross-domain coverage. Silverfort’s scope doesn’t include:
- Asset management
- Data encryption at rest
- Policy enforcement
- Third-party vendor oversight
Here’s the reality most vendors avoid: Silverfort is not a compliance framework. It’s an enforcement tool. To get insured in 2025, your environment must reflect a mature security lifecycle.
Writer’s fingerprint: This is where many teams get it wrong. They think buying a Zero Trust tool equals automatic coverage. But insurance doesn’t reward intentions—it rewards verifiable outcomes. And in most cases, that means proving you’ve thought through everything else Silverfort doesn’t cover.
Table: What Insurers Want to See in 2025
| Requirement | Addressed by Silverfort | Requires Additional Tools |
|---|---|---|
| Identity Access Management (IAM) | ✅ Strong | 🔄 Possibly |
| Phishing Training & Simulation | ❌ Not Included | ✅ Yes |
| Endpoint Detection & Response (EDR) | ❌ Not Included | ✅ Yes |
| Incident Response Playbooks | ❌ Not Included | ✅ Yes |
| Vendor Risk Assessments | ❌ Not Included | ✅ Yes |
| Backup and Recovery Testing | ❌ Not Included | ✅ Yes |
4. How to Improve Cyber Insurance Eligibility When Using Silverfort
4.1 Complementary Controls: EDR, SIEM, Employee Training
Jillian, an operations VP at a logistics firm in Tulsa, proudly presented their Silverfort setup to a cyber insurance auditor. But when asked about phishing defenses and recovery testing, her confidence wavered. “We’ve locked down identity access,” she said. “But… we don’t do phishing drills. And our backups?” The auditor took notes. That quote didn’t make it into the final report—but the premium increase did.
Cyber insurance coverage with Silverfort becomes more insurable when paired with other security controls that fill the gaps Silverfort leaves behind.
Here’s what works best alongside Silverfort:
- EDR (Endpoint Detection & Response): Detects malware, ransomware, and compromised devices that MFA can’t prevent.
- SIEM (Security Information and Event Management): Centralizes logs, enables alerts, and provides the forensic trail insurers love.
- Employee Awareness Training: Targets the #1 risk vector—human error. Insurers now expect phishing simulations and mandatory retraining.
According to a 2025 NAIC bulletin, insurance eligibility is “heavily contingent on demonstrable layered defense measures that include, but are not limited to, identity security, endpoint monitoring, and human-centric risk reduction.”
Table: Control Synergy with Silverfort
| Control Type | Silverfort Native? | Needed for Insurance? |
|---|---|---|
| MFA for legacy systems | ✅ Yes | ✅ Yes |
| Device behavior alerts | ❌ No | ✅ Yes |
| Email phishing filters | ❌ No | ✅ Yes |
| Security log correlation | ❌ No | ✅ Yes |
| Phishing simulations | ❌ No | ✅ Yes |
Pro Tip: Document and share how your security tools interact. Insurers value interoperability more than isolated tools. Showing Silverfort connected to SIEM = real points earned.
4.2 Insurance Readiness Checklist (2025 Standards)
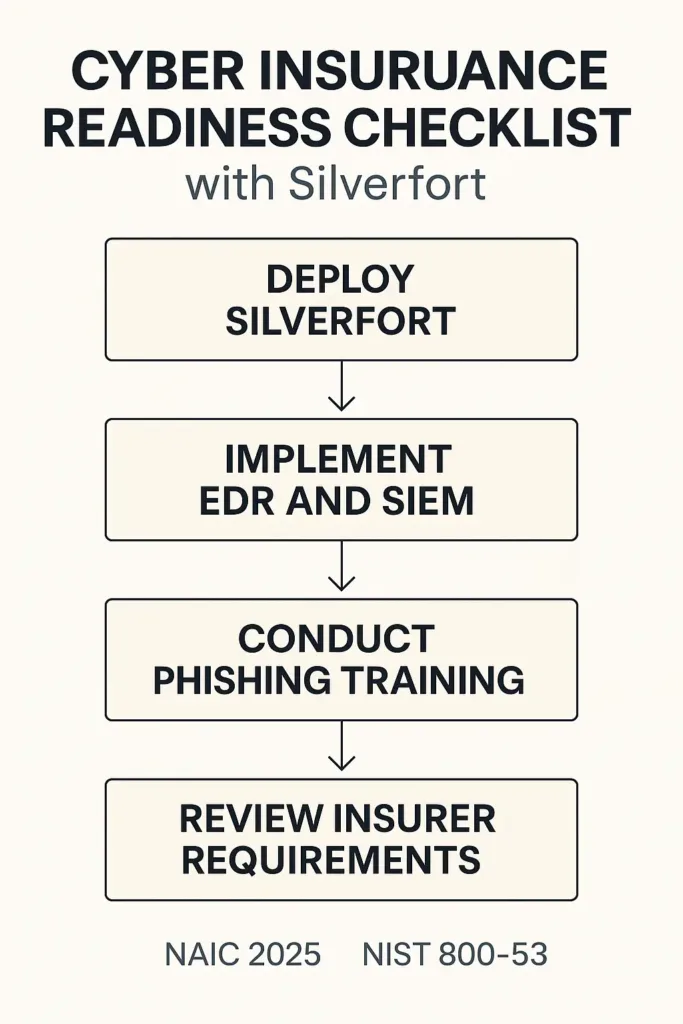
The biggest risk in cyber underwriting isn’t a lack of tools—it’s a lack of proof. To improve cyber insurance coverage with Silverfort, you must anticipate what auditors ask and have it documented.
Here’s a 2025-ready checklist to help:
Cyber Insurance Readiness Checklist (Silverfort Environment)
✅ MFA enabled across all user tiers, including admins and contractors
✅ Identity logs centrally stored (via SIEM or native API export)
✅ EDR deployed on 100% of endpoints
✅ Phishing training conducted and logged quarterly
✅ Recovery tests validated and timestamped within last 6 months
✅ Policy mapping to NIST 800-53 or CIS v8 documented
✅ Third-party vendors assessed using a formal risk scoring system
✅ At least one tabletop incident response exercise run in 12 months
Many insurance applications now include fields like:
- “Do you simulate phishing?”
- “When was your last backup tested?”
- “Do you monitor lateral movement?”
A “yes” backed by Silverfort logs and a layered stack is more powerful than any marketing statement.
Writer’s fingerprint: Here’s the catch. Many companies believe they’re protected simply because they’ve bought the right tech. But insurance isn’t about the gear—it’s about discipline. Documentation, drills, and dashboards count more than invoices.
4.3 What to Tell Your Insurer During Risk Assessment
During a risk assessment, it’s not just about having cyber insurance coverage with Silverfort—it’s about explaining how you use it.
What you should say:
- “Silverfort enforces MFA on all systems, including those not supported by native identity providers.”
- “It’s integrated with our SIEM, feeding real-time access logs for continuous monitoring.”
- “We’ve used Silverfort logs to refine our access policies based on behavior patterns.”
What you shouldn’t say:
- “We use Silverfort, so we don’t need endpoint protection.”
- “Our Zero Trust setup handles everything.”
- “We’ve bought it, but we’re still rolling it out.”
Insurers know the difference between deployment and adoption. Show policies, diagrams, reports—not just product names.
Dialogue: Underwriter vs CISO
Underwriter: “Does your MFA cover RDP access to legacy servers?”
CISO: “Yes. Silverfort enforces that, and we audit logins weekly via our SIEM.”
Underwriter: “That’s what I needed to hear.”
Pro Tip: Translate your controls into outcomes. Instead of saying “we have MFA,” say “unauthorized access attempts have dropped by 42% since deploying Silverfort.”
5. Common Misconceptions About Cyber Insurance Coverage Silverfort
5.1 “We Have Silverfort, So We’re Fully Covered”
Earlier this year, a tech startup in Portland called their broker after a ransomware incident, confident they’d be reimbursed. “We use Silverfort,” said the CTO. “We’ve got Zero Trust.” The response was sobering: “Yes, but your backups failed, and you had no phishing training logs. That’s not covered.”
One of the most dangerous misconceptions about cyber insurance coverage with Silverfort is assuming it offers complete protection. Silverfort addresses identity-centric risk, but most insurance claims in 2025 stem from multifactor failures—like phishing, poor patching, or insider error.
Silverfort enforces MFA and blocks lateral movement. That’s valuable. But your insurer evaluates dozens of other factors before approving or denying a claim. Without endpoint protection, awareness training, or tested recovery protocols, coverage can be denied—even if identity controls are airtight.
NAIC 2025 Model Law, Section 6, requires “reasonable administrative, technical, and physical safeguards.” Silverfort helps with technical—but not the others.
5.2 “Silverfort Guarantees Lower Premiums”
Insurers don’t discount premiums based on product logos. They do it based on risk reduction outcomes—which means logging, policy enforcement, and evidence of proactive use.
Another persistent myth: cyber insurance coverage with Silverfort automatically reduces your costs. While it may help in scoring identity maturity, premiums are driven by broader metrics like:
- Recovery time objectives
- Insider threat response
- Patch management frequency
- Supply chain controls
If Silverfort is poorly implemented or only used on part of your infrastructure, it could actually backfire—creating a false sense of security with no real underwriting benefit.
Writer’s fingerprint: This is where things get awkward in board meetings. Executives expect cost drops after buying Zero Trust tools. But when the quote arrives and it’s higher than last year, everyone stares at the CISO. Reality? Tools ≠ assurance. Evidence does.
5.3 “Silverfort Makes Other Tools Obsolete”
Silverfort is often misrepresented as a complete Zero Trust platform, when in fact it’s a powerful identity access enforcement engine. Believing it eliminates the need for:
- EDR platforms like CrowdStrike or SentinelOne
- Email security gateways like Proofpoint
- SIEM systems like Splunk or Microsoft Sentinel
…is not just wrong—it’s risky.
Cyber insurance coverage with Silverfort only becomes meaningful when integrated into a broader ecosystem. Underwriters expect tool synergy, not tool substitution.
A mature 2025 security posture typically includes:
- Identity + Endpoint + Email + Network monitoring
- Real-world simulations (phishing, ransomware, backup recovery)
- Framework mapping (NIST, CIS, NAIC)
Table: Myth vs Reality of Silverfort in Cyber Insurance
| Misconception | Reality |
|---|---|
| “Silverfort = Full Coverage” | ❌ Partial — needs layered controls |
| “Silverfort reduces premiums automatically” | ❌ Only if integrated and documented |
| “Silverfort replaces other tools” | ❌ Complementary, not a substitute |
| “Zero Trust means insurance approval” | ❌ Depends on risk outcomes, not just strategy |
| “Logs aren’t necessary if Silverfort is used” | ❌ Logs and audit trails are critical for claim validation |
5.4 “Silverfort Will Impress Any Underwriter”
Let’s be honest—underwriters in 2025 are hard to impress. They’ve seen it all: from cloud-native stacks to AI-generated SOCs. Dropping the name “Silverfort” in a risk assessment might raise eyebrows—but it won’t raise your score unless it’s operationally embedded.
What underwriters really want:
- Documented MFA coverage across legacy systems
- Logs showing attempted access blocks
- Alerts configured and monitored
- Human behavior controls (training, insider threat detection)
- Recovery drill evidence
Silverfort can support all of that—but doesn’t do it alone.
Pro Tip: Don’t present Silverfort as a magic bullet. Present it as a well-deployed control that solves a specific problem—identity sprawl and lateral access—within a documented broader defense strategy.
6. 2025 Compliance Snapshot: Cyber Insurance Laws and Silverfort
6.1 NIST 800-53, HIPAA, and State-Level Requirements
In early 2025, Rachel, a compliance lead at a mid-size hospital in Des Moines, was preparing documentation for a cyber insurance renewal. “We’ve deployed Silverfort across all legacy systems,” she noted. But when the insurer asked for their HIPAA safeguards mapping, and how Silverfort aligned with NIST 800-53, she wasn’t ready. Her tools were strong—but her documentation wasn’t.
Cyber insurance coverage with Silverfort aligns best with access control and identification/authentication requirements. But U.S. insurers increasingly evaluate security controls through the lens of regulatory compliance.
How Silverfort aligns with major 2025 cybersecurity frameworks:
| Requirement Area | HIPAA | NIST 800-53 | Silverfort Role |
|---|---|---|---|
| Access Control (164.312(a)(1)) | ✅ Required | AC-2, AC-3, AC-5 | ✅ Enforced via MFA |
| Unique User Identification | ✅ Required | IA-2, IA-5 | ✅ Identity visibility |
| Audit Controls | ✅ Required | AU-2, AU-6, AU-12 | ⚠️ Partial (via SIEM) |
| Security Incident Procedures | ✅ Required | IR-4, IR-5 | ❌ Not handled |
| Device and Media Control | ✅ Required | MP-2, MP-6 | ❌ Out of scope |
Silverfort plays a complementary role in fulfilling these standards. But to pass insurer audits in 2025, businesses must show comprehensive adherence, not isolated tool deployment.
Citation – U.S. Department of Health & Human Services (HHS), 2024 Update: “Security tools must demonstrate operational effectiveness across technical, physical, and administrative safeguards to satisfy HIPAA compliance and qualify for risk-adjusted cyber insurance premiums.”
Pro Tip: Don’t just deploy Silverfort—document how it satisfies specific compliance clauses. Tie each control to a requirement ID (e.g., AC-2 or 164.312(a)) and attach usage logs or screenshots.
6.2 How Insurers Use These Standards to Evaluate Clients
Insurers in 2025 no longer rely on vague security self-assessments. They cross-reference claims of protection with compliance frameworks—primarily NIST 800-53, HIPAA, and the NAIC Cybersecurity Model Law. If your use of Silverfort can’t be mapped to these frameworks, it may be dismissed as insufficient.
Here’s how insurers use these frameworks in real-world assessments:
- NIST 800-53 is frequently referenced by insurers to assess the maturity and consistency of your security controls across systems.
- HIPAA: Mandatory for healthcare clients; insurers look for full administrative and technical alignment.
- State-level laws (e.g., NYDFS, CCPA): Require proof of access control, encryption, audit logging—Silverfort supports parts of these but not all.
Checklist: How Insurers Map Your Silverfort Usage
✅ Can you show enforced MFA across all asset tiers?
✅ Are logs centrally stored and reviewed monthly?
✅ Have you clearly aligned your Silverfort configurations with NIST control families such as AC-2 (account management), IA-2 (authentication), and AU-6 (audit review)?
✅ Is Silverfort integrated with IR protocols (via SIEM or SOAR)?
❌ Have you addressed gaps outside of Silverfort’s scope—like building security protocols and user behavior awareness training?
Writer’s fingerprint: This is where the technical meets the bureaucratic. A CISO might say “We’re secure.” But the insurer replies, “Show me how that aligns with NIST IR-4.” Tools like Silverfort help, but only if someone takes the time to translate action into compliance.
Table: Compliance Relevance of Silverfort by Framework
| Framework | Relevance of Silverfort | Notes |
|---|---|---|
| NIST 800-53 | ✅ High (Identity layer) | Must be mapped and logged |
| HIPAA | ✅ Moderate | Only covers technical safeguards |
| NAIC Model Law | ✅ Partial | Needs admin & physical safeguards too |
| NYDFS Cyber Regs | ✅ Partial | Strong on access, weak on backup/logging |
| CISA Zero Trust | ✅ High | Identity pillar support, not full stack |
7. Final Thoughts: Is Silverfort Enough for Peace of Mind?
7.1 Cyber Insurance Coverage Silverfort Enhances—But Doesn’t Complete
Silverfort unquestionably reinforces access security. By enforcing adaptive multi-factor authentication (MFA) across diverse systems, it helps reduce identity-based attack surfaces—especially in hybrid environments. This matters for underwriters, as identity assurance is a key risk scoring element under frameworks like NIST 800-53 and HIPAA’s technical safeguard rules. However, here’s what often gets overlooked in boardroom discussions: Silverfort doesn’t function in a vacuum.
Take a real-world example: Jason, a CIO for a mid-sized logistics company in St. Louis, had recently passed an internal audit thanks to their Silverfort rollout. But when the cyber insurance renewal packet landed on his desk, one line from the broker changed everything:
“What compensating controls do you have if Silverfort gets bypassed?”
That moment exposed a blind spot. Silverfort covered identity enforcement. But not phishing simulations, nor SIEM integration, nor endpoint containment. The broker wasn’t looking for a shiny tool—they were looking for systemic resilience.
Pro Tip
Cyber insurers rarely underwrite software—they underwrite preparedness. Silverfort strengthens part of the posture, but alone, it’s not an insurance strategy.
7.2 When Silverfort Helps—and When It’s Not Enough
Yes, Silverfort supports several cybersecurity goals that insurers recognize—centralized access policies, identity-centric MFA, and alignment with AC-2, IA-2, and AU-6 controls. That’s a strong start. But insurers don’t view identity protection as the full story.
Here’s the truth: most carriers evaluate clients through a broader, layered lens. That means endpoint hardening, backup validation, human error mitigation, and response readiness—all aspects where Silverfort plays only a minor or indirect role.
Let’s break this down:
| Security Domain | Does Silverfort Cover It? | Insurer’s Expectation (2025) |
|---|---|---|
| Identity & Access | ✅ Strong MFA & policy control | Required baseline |
| Email Phishing Defense | ❌ Not covered | Must demonstrate simulation + training |
| Endpoint Protection | ❌ Requires EDR integration | Required for ransomware and breach response |
| Incident Response Playbooks | ❌ Outside Silverfort scope | Must be documented, tested, and updated |
| Backup & Recovery | ❌ Not addressed | Required for data breach coverage |
Checklist: Can Silverfort Alone Meet These Insurance Must-Haves?
- MFA enforcement beyond identity systems?
- Anti-phishing simulation results available?
- Documented disaster recovery testing logs?
- SIEM/EDR logs linked to user activity?
- Evidence of continuous employee training?
That’s not a failure of Silverfort—it’s a reality check. As of 2025, insurers follow frameworks like the NAIC Cybersecurity Model Law and NIST CSF 2.0, which both emphasize defense-in-depth.
Quote to Remember
“Identity is just one layer. Underwriters insure the stack.” — Former NAIC advisor, Cyber Risk Roundtable 2024
7.3 Bridging the Gap: Turning Silverfort Into a Stronger Insurance Ally
So, how do you make Silverfort a meaningful part of your insurability plan—not just a checkbox?
Here’s what brokers and auditors actually want to see:
- A written cybersecurity policy that names Silverfort as part of your access control strategy.
- Integration proof between Silverfort and SIEM/IR tools (e.g., Splunk, CrowdStrike, SentinelOne).
- Clear mapping of Silverfort controls to compliance obligations under HIPAA, NIST, or state-level mandates like NYDFS.
- Documentation that you’ve tested fallback options—because even strong IAM can be bypassed.
And finally, a mindset shift: Silverfort is a powerful brick in the wall, but not the wall itself.
Bottom Line?
Silverfort can absolutely improve your cyber risk posture—but it won’t, on its own, unlock premium discounts or ensure full eligibility. Peace of mind doesn’t come from a single platform. It comes from showing your insurer that you’ve thought beyond identity, and built a resilient, multi-layered ecosystem.